WordPress is the most popular content management system, powering over 40% of websites. However, its popularity also makes WordPress sites a target for attacks. One common type of attack is brute-force attempts to guess login credentials. To protect your site, it’s essential to limit login attempts. Let’s begin the comprehensive guide on How to Limit Login Attempts in WordPress.
Should You Limit Login Attempts in WordPress?
Yes, limiting login attempts in WordPress is highly recommended for security reasons.
Limiting login attempts in WordPress is a crucial security measure to protect your website from brute-force attacks. Here are some reasons why you should limit login attempts and how to implement this feature:
Why You Should Limit Login Attempts
1. Prevent Brute Force Attacks
Brute force attacks involve repeated attempts to guess a user’s password. By limiting login attempts, you can significantly reduce the likelihood of an attacker successfully gaining access to your website.
2. Enhance Website Security
Limiting login attempts adds an extra layer of security to your WordPress site. This measure ensures that even if someone tries to break in, they have a limited number of tries before being locked out.
3. Reduce Server Load
Continuous login attempts can put a strain on your server, slowing down your website. By limiting the number of login attempts, you can mitigate this issue and maintain optimal site performance.
4. Protect User Accounts
If your website allows user registrations, limiting login attempts can help protect your users’ accounts from unauthorized access. This measure reassures your users that their data is secure.
Default WordPress Login Settings
In a standard WordPress installation, the default login settings are relatively permissive. For example:
- Unlimited Login Attempts: WordPress allows users to make an unlimited number of login attempts by default. This means that attackers can keep trying different username and password combinations indefinitely.
- No Delay Between Login Attempts: No delay or rate is limiting between login attempts, making it easier for attackers to conduct brute-force attacks.
- No Lockout or IP Blocking: WordPress does not automatically lock out users or block IP addresses after a certain number of failed login attempts.
Importance of Login Attempt Limits
Limiting login attempts is crucial for several reasons:
- Protection Against Brute Force Attacks: Attackers use automated tools to guess login credentials. Limiting attempts makes it harder for them to succeed.
- Preventing Credential Stuffing: Attackers use credentials obtained from data breaches on other sites to gain access to WordPress sites. Limiting attempts reduces the risk of successful attacks.
- Mitigating DDoS Attacks: Some attacks target the login page with a large number of login attempts, overwhelming the site. Limiting attempts helps minimize the impact of such attacks.
- Protection Against User Enumeration: WordPress provides different error messages for incorrect usernames and passwords, allowing attackers to determine valid usernames. Limiting attempts reduces this risk.
How to Limit Login Attempts in WordPress Using Plugin
The “Limit Login Attempts Reloaded” plugin is a powerful tool that can help you enhance the security of your WordPress site by limiting the number of login attempts allowed for each user. In this guide, we’ll walk you through the process of installing, configuring, and using this plugin to protect your site from brute-force attacks.
Installing the Plugin
- Navigate to the Plugins Page: In your WordPress dashboard, go to Plugins > Add New.
- Search for the Plugin: In the search bar, type “Limit Login Attempts Reloaded.”
- Install the Plugin: Click on the “Install Now” button next to the plugin name.
- Activate the Plugin: Once the installation is complete, click on the “Activate” button to activate the plugin.
Configuring the Plugin
- Access the Plugin Settings: After activating the plugin, go to Settings > Limit Login Attempts to access the plugin settings.
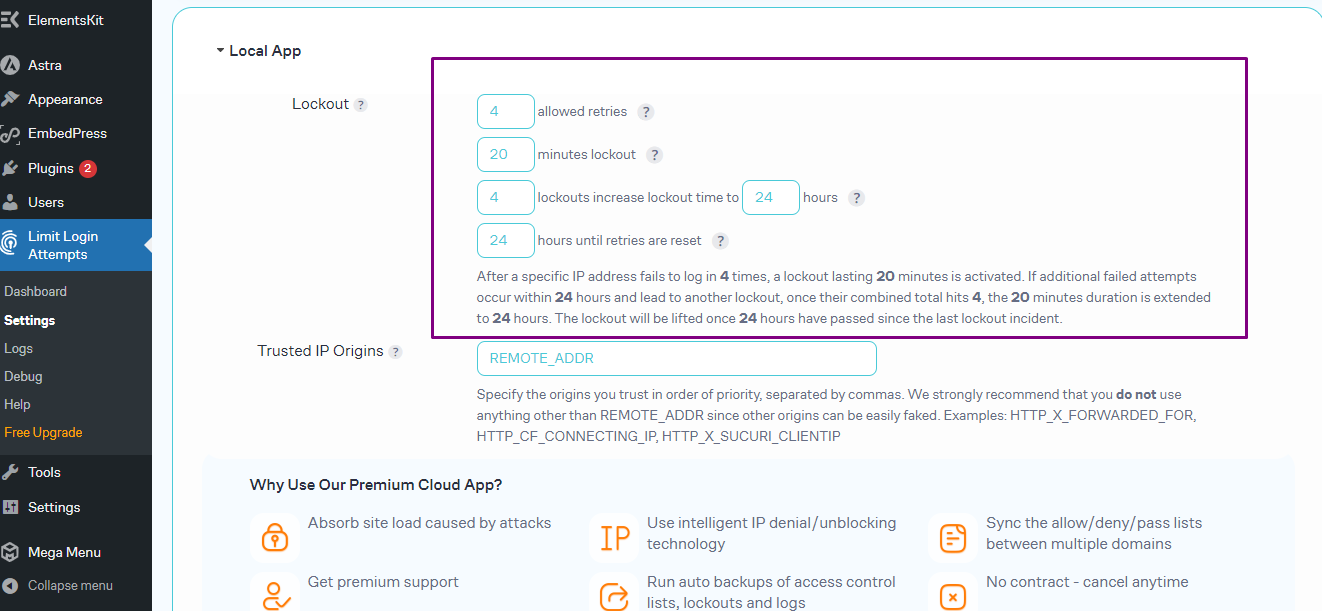
- Set the Maximum Login Attempts: In the “Login Attempts” section, specify the maximum number of login attempts allowed before a user is locked out.
- Set the Lockout Duration: Specify the duration for which a user will be locked out after exceeding the maximum login attempts.
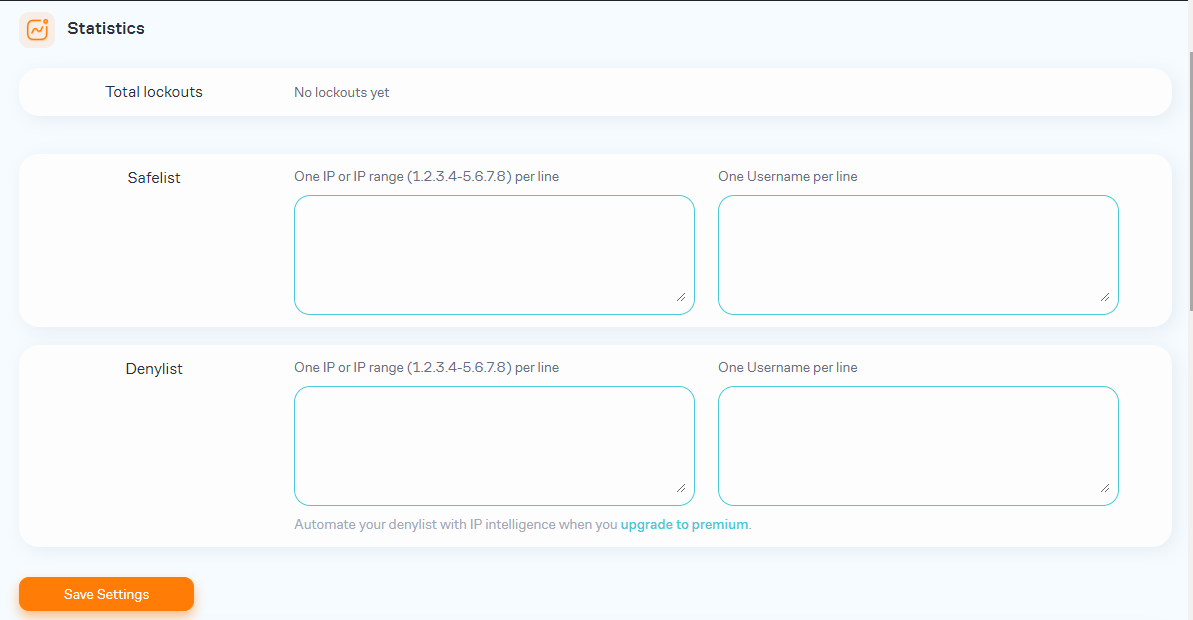
- Configure Other Settings: You can also configure other settings, such as the lockout message, notification options, and IP whitelist/blacklist.
Option Description Safelist Allows you to specify IP addresses or usernames that should be exempt from the login attempt limits. Denylist/Blacklist Allows you to specify IP addresses or usernames that should be blocked from accessing the site. - Save Changes: Click on the “Save Changes” button to save your settings.
Testing the Plugin
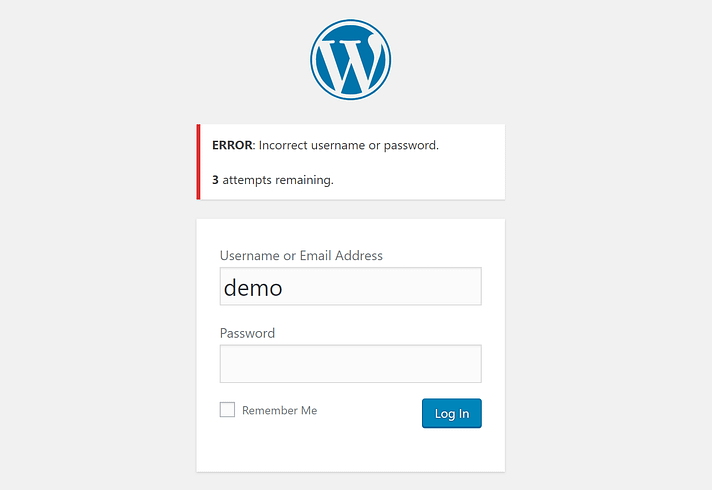
- Attempt to Log In with Incorrect Credentials: To test the plugin, try to log in to your WordPress site with incorrect credentials multiple times.
- Verify Lockout Behavior: After exceeding the maximum login attempts, you should be locked out of your account for the specified duration.
- Verify Notification Options: If you have configured notification options, you should receive notifications about the lockout.
Additional Security Measures
- Use CAPTCHA: Implement CAPTCHA to deter automated login attempts further.
- Use a Firewall: Use a firewall to block suspicious login attempts.
- Monitor Logs: Use tools like Fail2Ban to monitor logs and block IP addresses that make too many failed login attempts.
- Use wp_login_failed Hook: Implement custom code to block users after a certain number of failed login attempts.
- Limiting Login Attempts: Best Practices: Implement a whitelist for IP protection, tailored error messages, and regular software updates for enhanced security.
Conclusion:
In conclusion, limiting login attempts in WordPress is a critical step in securing your website against unauthorized access and brute-force attacks. By using the “Limit Login Attempts Reloaded” plugin, you can effectively protect your site by setting limits on failed login attempts, configuring lockout durations, and monitoring login activity.
You May Also Like:
How to Fix WordPress Not Sending Email Issue
How to convert PSD to WordPress
Additionally, implementing other security measures such as two-factor authentication, regular software updates, and IP whitelisting/blacklisting can further enhance the security of your WordPress site. By taking these proactive steps, you can significantly reduce the risk of security breaches and ensure the safety of your website and its data.