WordPress, a widely used content management system, is renowned for its open-source design, flexibility, and user-friendly interface. Powering over 40 percent of websites globally, its popularity, unfortunately, exposes users to a plethora of security risks. In this guide, we’ll delve into the crucial topic of the Latest WordPress Vulnerabilities and security issues & how to fix them.
Mitigating Security Vulnerabilities: The Imperative
Your WordPress website is susceptible to various security threats such as bots, brute force attacks, and backdoor intrusions, all of which can have dire consequences. Compromised security not only jeopardizes sensitive user information but also erodes trust and can lead to a decline in site visibility. Even the most meticulous SEO optimization cannot salvage a compromised website.
Is WordPress Secure Enough?
While WordPress boasts numerous merits, its security is not infallible. Relying solely on common solutions like specialized plugins is insufficient. Recognizing this, a robust security strategy must transcend simplistic measures. Although WordPress hacks often make headlines, proactive measures can shield your site from falling prey to security breaches.
The Importance of Closing All Potential Security Vulnerabilities
Closing all potential security vulnerabilities is paramount for several reasons:
- Protecting Sensitive Data: Your website likely stores a wealth of sensitive information, including user credentials, payment details, and personal data. Failure to secure vulnerabilities could lead to unauthorized access and subsequent data breaches, resulting in identity theft, financial fraud, and legal liabilities.
- Ensuring Continuity of Service: Security vulnerabilities can be exploited to disrupt the normal functioning of your website. Attackers might launch denial-of-service (DoS) attacks, overwhelming your server with malicious traffic and rendering your site inaccessible to legitimate users.
- Preserving Trust and Reputation: A security breach not only compromises your data but also undermines the trust and confidence of your users. By prioritizing security measures, you demonstrate a commitment to safeguarding user information and maintaining their trust.
- Compliance with Regulations: Depending on your industry and geographic location, you may be subject to various regulatory requirements governing data protection and cybersecurity. Failing to address security vulnerabilities can result in non-compliance penalties, fines, and legal consequences.
- Preventing Financial Losses: Recovering from a security breach can be costly, involving expenses related to forensic investigations, data recovery, legal fees, and potential regulatory fines. Additionally, downtime resulting from an attack can lead to loss of revenue and business opportunities.
Latest WordPress Vulnerabilities and Security Issues & Solutions
Today, we’re diving deep into 13 of the latest WordPress vulnerabilities and showing you how to fix them in simple, human language. There is no tech jargon here, just clear steps to keep your website safe and sound.
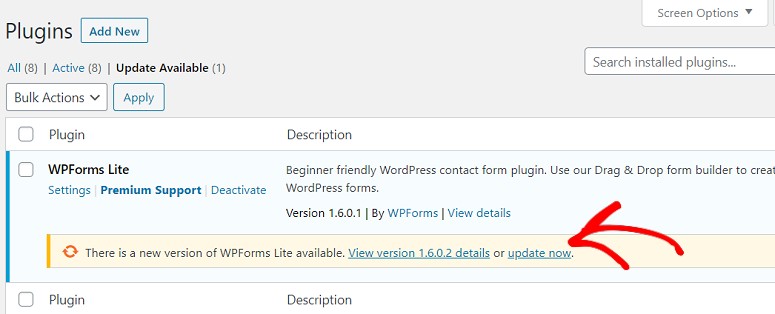
1. Outdated WordPress, Themes, and Plugins: This is like leaving your door wide open! Always keep your WordPress core, themes, and plugins updated to the latest versions. They often include security patches to fix known vulnerabilities.
Fix: Head to your WordPress dashboard, click on “Updates,” and update everything in sight!
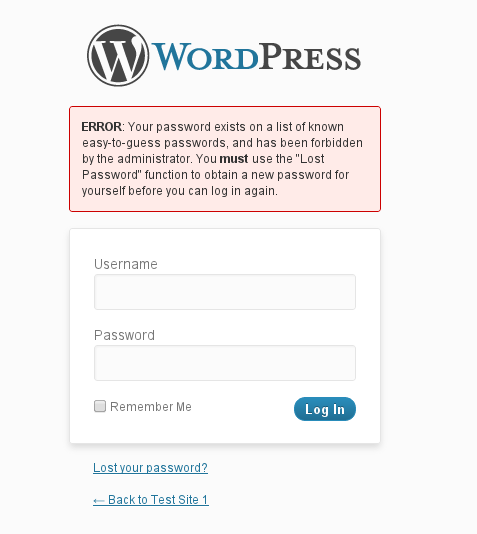
2. Weak Passwords: Imagine using “password123” as your lock code. Not secure, right? The same goes for your website. Use strong, unique passwords for all your accounts, and consider using a password manager.
Fix: Create complex passwords with a mix of uppercase and lowercase letters, numbers, and symbols. Consider two-factor authentication for an extra layer of security.
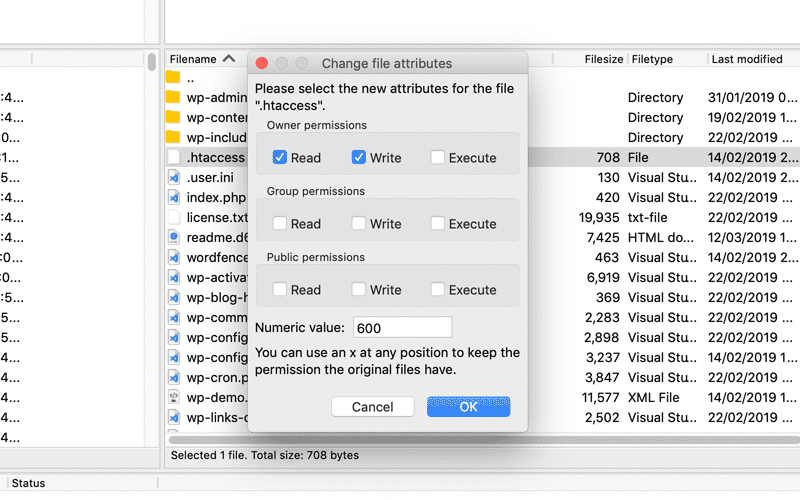
3. Insecure File Permissions: Think of file permissions as bouncers at a club. They control who can access and modify your website files. Keep them tight!
Fix: Use a secure file permissions plugin or manually set them using your File Transfer Protocol (FTP) program. Aim for 755 for files and 705 for directories.
4. Malicious Plugins and Themes: Not all plugins and themes are created equal. Download from trusted sources and check reviews before installing anything.
Fix: Stick to well-established developers with good reputations. Regularly scan your plugins and themes for vulnerabilities using a security plugin.
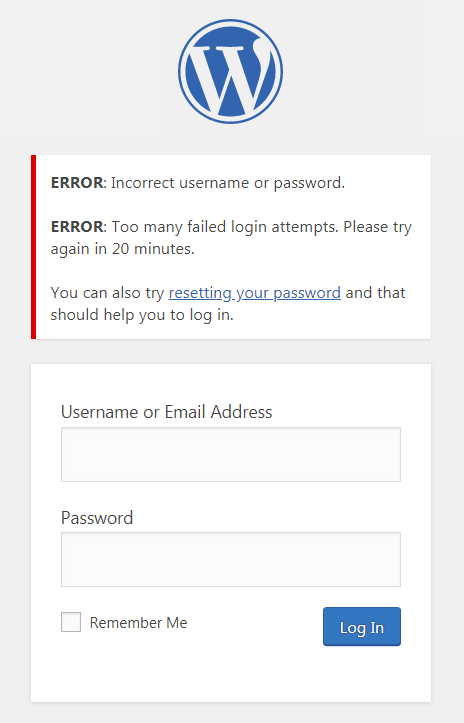
5. Brute-Force Login Attempts: Hackers can use automated tools to guess your password repeatedly. Make it harder for them!
Fix: Enable strong password policies, limit login attempts, and use a security plugin with login attempt monitoring.
6. Unnecessary User Accounts: The fewer accounts, the fewer potential entry points for hackers. Delete inactive users and assign appropriate permissions to the remaining ones.
Fix: Regularly review user accounts and remove any that are no longer needed. Use the principle of least privilege, giving users only the access they need.
7. Unpatched PHP Version: Just like WordPress, your PHP version needs regular updates to stay secure.
Fix: Check with your hosting provider to see if they offer automatic PHP updates. If not, ask them to update it for you or learn how to do it yourself.
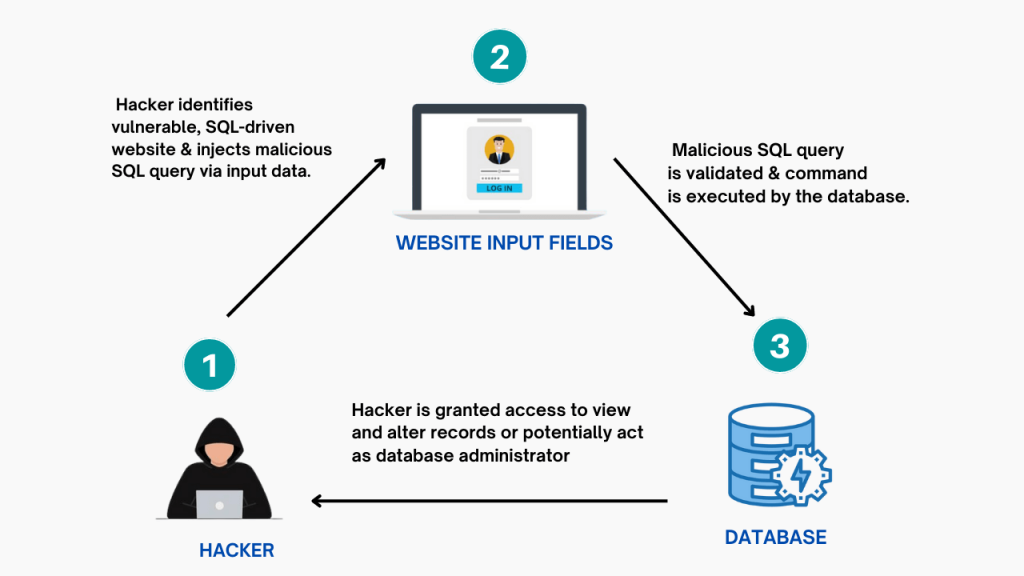
8. SQL Injection Attacks: Hackers can inject malicious code into your website through forms or search bars. Keep your website patched and use input validation plugins.
Fix: Update your WordPress core and plugins regularly. Use input validation plugins to sanitize user input before it reaches your database.
9. Cross-Site Scripting (XSS) Attacks: Hackers can inject malicious scripts into your website that can steal user information or redirect them to harmful sites.
Fix: Keep your WordPress core and plugins updated. Use output escaping plugins to sanitize any data displayed on your website.
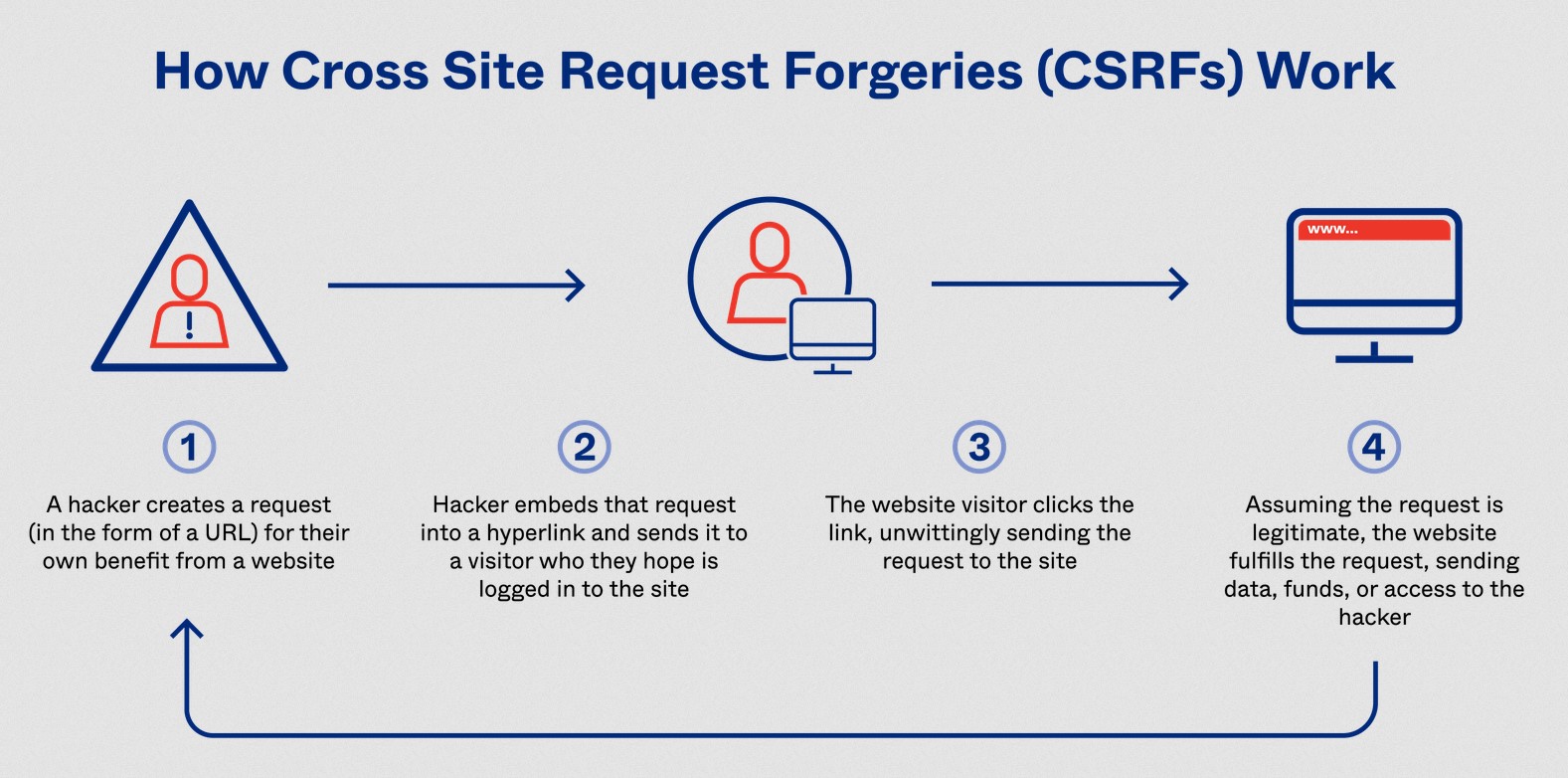
10. Cross-Site Request Forgery (CSRF) Attacks: Hackers can trick users into performing unwanted actions on your website. Use security plugins with CSRF protection.
Fix: Install a security plugin with CSRF protection enabled. Update your WordPress core and plugins regularly.
11. File Inclusion Vulnerabilities: Hackers can exploit weaknesses in your website to include malicious files. Follow secure coding practices and keep your software updated.
Fix: Use well-coded plugins and themes from reputable developers. Update your WordPress core and plugins regularly.
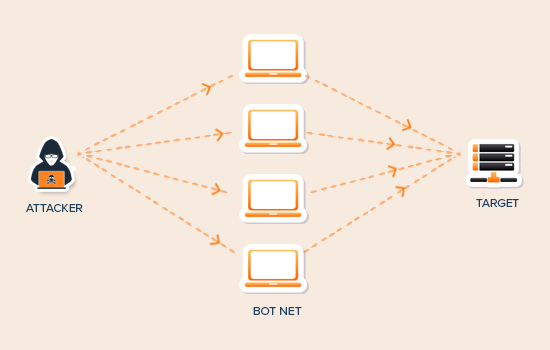
12. Denial-of-Service (DoS) Attacks: Hackers can overload your website with traffic, making it unavailable to legitimate users. Use a security plugin with DDoS protection.
Fix: Choose a reliable hosting provider with DDoS protection features. Consider using a Content Delivery Network (CDN) to distribute your website traffic.
13. SEO Spam: Hackers can inject spammy links and keywords into your website to manipulate search engine rankings. Use an anti-spam plugin e.g. Spam Protection, Anti-Spam, FireWall by CleanTalk, and regularly monitor your website content.
Fix: Install an anti-spam plugin to automatically detect and remove spam comments and links. Regularly review your website content for suspicious changes.
Best Practices for WordPress Security
| Practice | Description | |
|---|---|---|
| Keep everything updated: Regularly update WordPress core, themes, and plugins to benefit from the latest security patches. | Minimizes the risk of exploiting outdated software vulnerabilities. | |
| Use strong, unique passwords: Avoid easy-to-guess passwords and enable two-factor authentication for added protection. | Prevents unauthorized access through brute-force attacks. | |
| Choose reputable plugins and themes: Download from trusted sources and check reviews before installing anything. | Reduces the risk of installing malicious plugins or themes. | |
| Limit user accounts and permissions: Only create user accounts when necessary and assign the least amount of permission required. | Minimizes potential damage if an account is compromised. | |
| Use a security plugin: These plugins offer website scanning, malware detection, firewall protection, and other security features. | Provides an extra layer of defense against various threats. | |
| Regularly backup your website: Having a backup allows you to quickly restore your website if it gets hacked or corrupted. | Ensures you can recover from unforeseen security incidents. | |
| Stay informed about security threats: Subscribe to security blogs and newsletters to stay updated on the latest threats and vulnerabilities. | Helps you proactively address potential security risks. |
By following these best practices and actively addressing vulnerabilities, you can significantly improve your WordPress website’s security and protect yourself from potential harm. Remember, website security is an ongoing process, so stay vigilant and take action to keep your website safe!